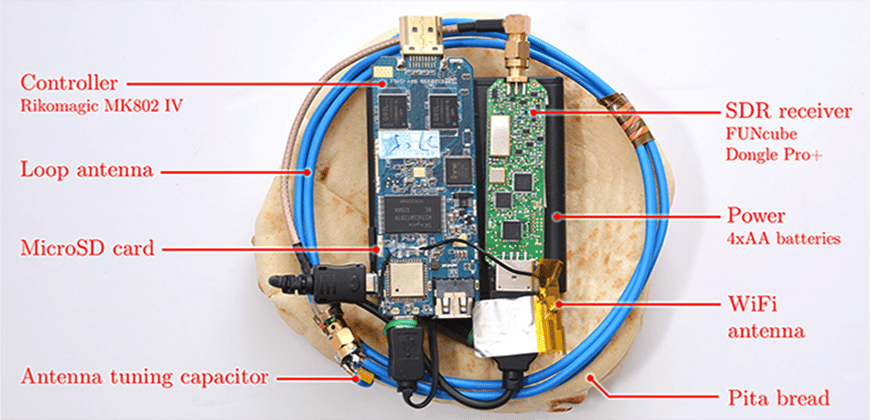
Warning: PITA Hacking Device – A Threat To Your Personal Computer’s Encrypted Key Strokes
This small device easily made from off-shelf parts can be a serious threat to your encrypted keystrokes. The “PITA” was named specifically after the popular pita bread, which the device can actually fit into.
An economically made hacking device, named PITA (Portable Instrument for Trace Acquisition) is small enough to fit virtually anywhere, and can steal your encrypted information off your laptop in a few seconds. The PITA device measures electromagnetic pulses from the keyboard then hackers use these keystrokes to decrypt secure documents, collect passwords, and steal credit card numbers. Obtaining the authentication keys on a computer gives the hackers free access to any and all data and otherwise secure documents, and if used in conjunction with another “sweeping” device, the entire contents can be swept off a computer.
A group of researchers from Tel Aviv University and Israeli research responsible for creating this PITA device, were able to extract keys in a few seconds from laptops of various models running GnuPG (a very popular open source encryption software). The researchers said “The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially-structured values inside the decryption software”.
Another alarm sounding off from this hacking device is that all computers omit these radio waves originating from the computers processor. Ethernet, Bluetooth, and Wi-Fi are “off the hook” as malefactors as this hacking device is using a side-channel attack, relying on unceasing electromagnetic emissions. This unconventional method of electromagnetic probing proves a threat to everyone – including businesses and everyday users.
Scientists Daniel Genkin, Lev Pachmanov, Itamar Pipman, and Eran Tromer have created this PITA hacking device, stating “Physical mitigation techniques of electromagnetic radiation include Faraday cages. However, inexpensive protection of consumer-grade PCs appears difficult”.
A Research team from the Tel Aviv University in Israel is expected to be presenting a paper in September at the Workshop on Cryptographic Hardware and Embedded System specifically detailing the most current channel attack exposing crypto keys. The team has said “Even when a cryptographic scheme is mathematically secure and sound, its implementations may be vulnerable to side-channel attacks that exploit physical emanations…” (It) “…can target commodity laptop computers. We have tested numerous laptop computers of various models and makes”.
Commonly used laptops and widely used RSA and ElGamal encryptions are susceptible to this hacking device, including those that use decryption using algorithms like fixed-window or sliding-window exponentiations. The nature of this hacking device makes it almost impossible to find a counter measure.
The actual hacking device is especially disturbing not only due to its small size (that can easily fit into a pita bread), but also the low manufacturing cost of under $300. A device this small can effortlessly be attached under table tops, is discreet enough for “walk-by” attacks, or can simply be concealed and brought into a secure business meeting. Mass production is a real concern for this hacking device using four AA batteries and off-the-shelf parts, but a consumer-grade radio receiver or a Software Defined Radio USB dongle is needed to complete that hacking setup, increasing the costs from $300. Researchers limited the range of the device to be 50 cm but using more expensive equipment including higher grade amplifiers would result in a longer range.
The PITA is dual functioning device that can operate in online mode or autonomous mode. In the online mode, the PITA uses low-bandwidth electromagnetic key-extraction via Wi-Fi for real-time streaming allowing optimized probe placement and adaptive recalibration of the carrier frequency and SDR gain adjustments. In Autonomous mode, the PITA records the digitized signal that measures the electromagnetic field around a designated carrier frequency onto its internal micro-SD card. A target computer is then used in an offline workstation to process the signals using signal analysis.
The researchers promptly notified the GnuPG developers about the attack, and together the researchers and developers adjusted the software’s algorithm. This hacker risk has been avoided… ( read more )
Article: “HCT America”
Editor: “Amy Jones”
Image: “TAU”